TABLE I.






TABLE II.
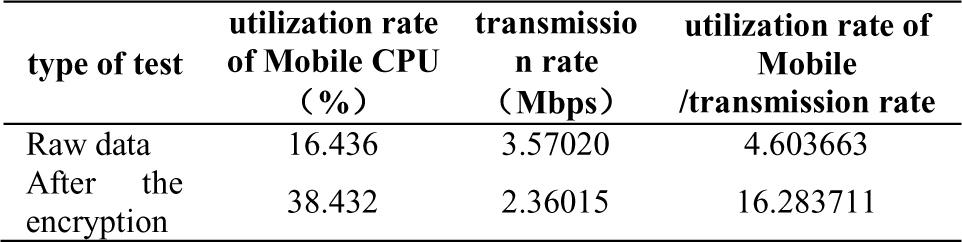
TABLE III.
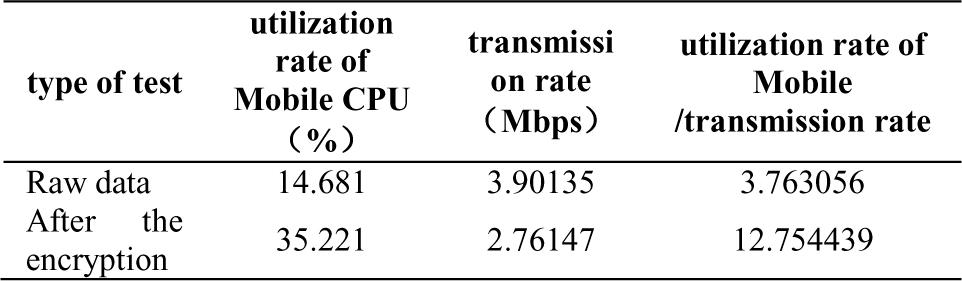
TABLE IV.
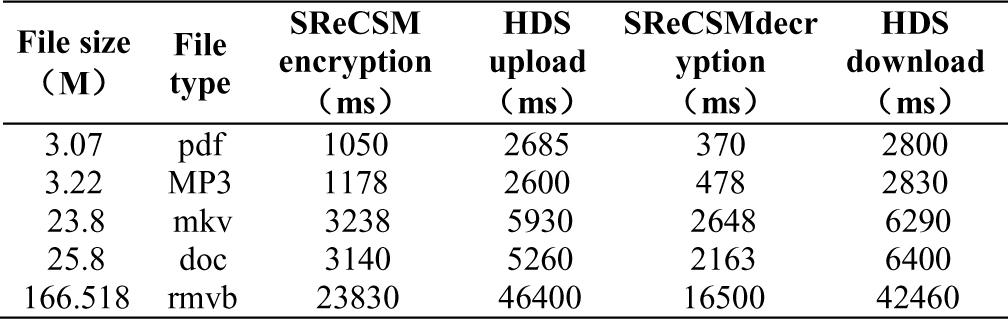
Figure 1.
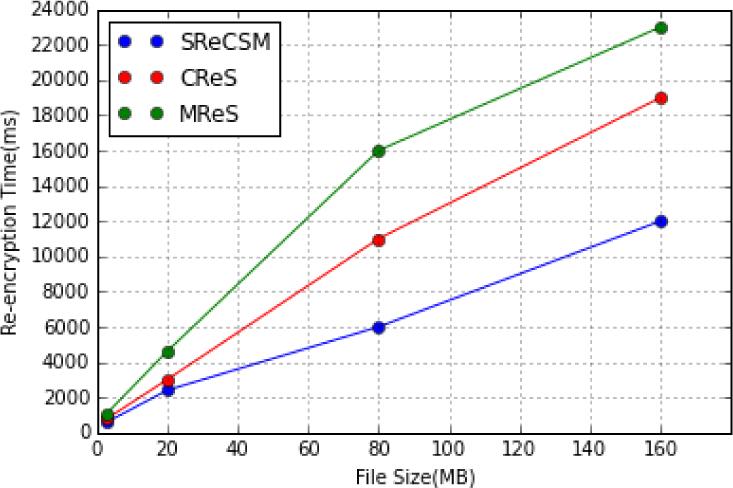
TABLE V.
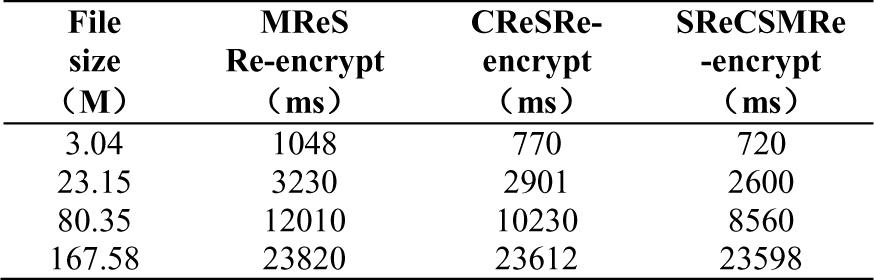
Figure 2.
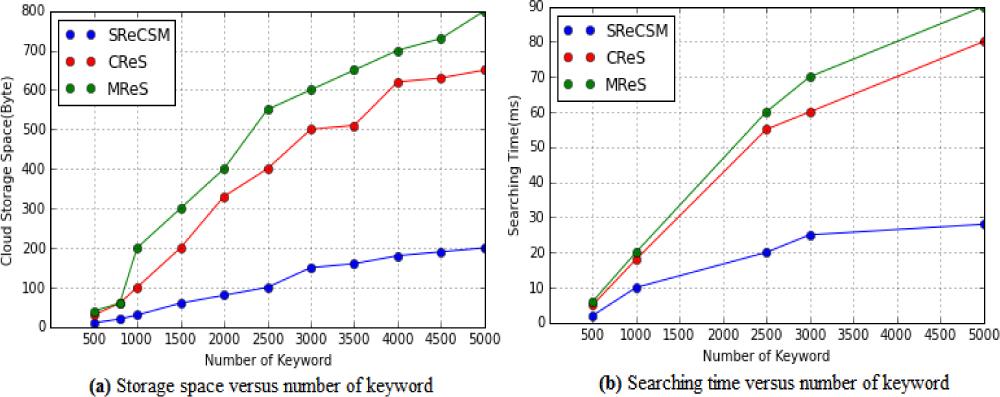
Figure 3.
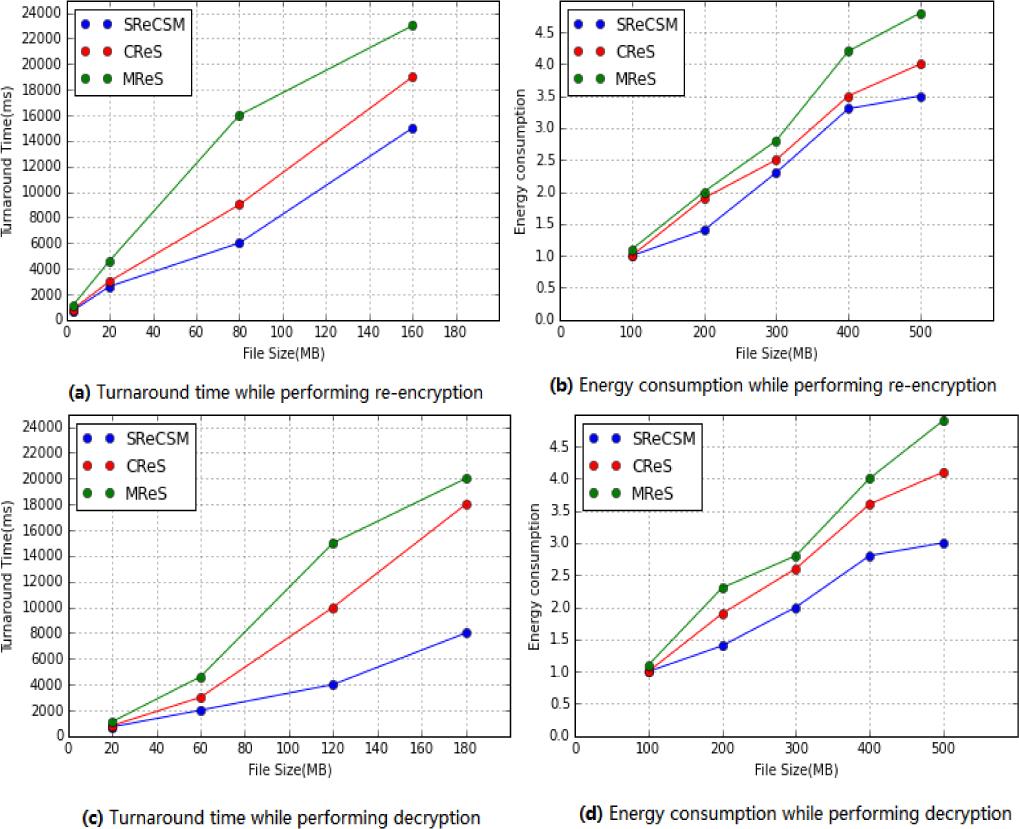
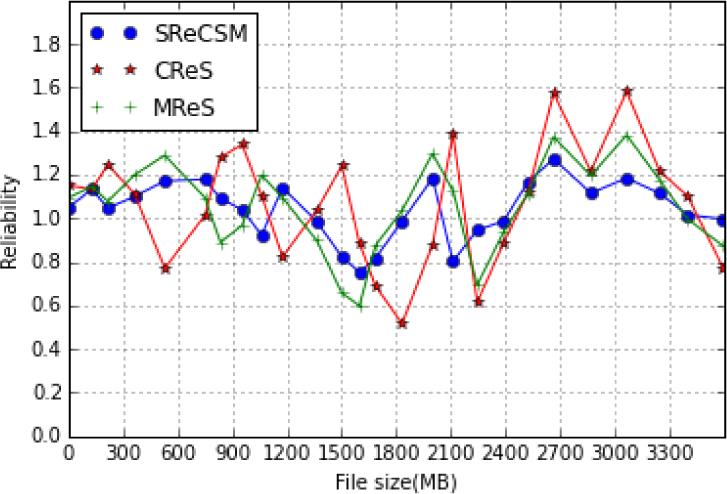
Figure 4.















© 2018 Wang Hui, Hong Bo, Tang Junyong, published by Xi’an Technological University
This work is licensed under the Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 License.